
Protect, detect and respond to advanced threats with endpoint detection and response (EDR)
As remote working surged in the past couple of years, so too did the increase and sophistication of endpoint attacks. As cybercriminals get more advanced, it’s now abundantly clear that protecting endpoints is more essential to an organisation’s network security than it ever was.
Endpoint detection and response (EDR) technologies provide the frontline defence needed to keep up with attacks that will continue to grow in frequency and size and are a vital part of any business’ cyber security arsenal. Why? Because they have been specifically designed to trace and investigate suspicious activities on the endpoint.
Where are the weaknesses?
IT leaders are increasingly focused on one of the weakest links in their chain – their employees and the devices they use in today’s mobile world.
Greater volumes of remote workers means greater volumes of bring your own device (BYOD) initiatives in workplaces. These span the more commonplace laptop and mobile to the newer but increasing inclusion of smartwatches and the Internet of Things (IoT). And here lies the potential for problems, because IT and cyber security teams have to solve the challenges that come with securing these devices to reduce the risks the business is consequently exposed to. And the truth of it is legacy security solutions just cannot keep up.
A newer, more sophisticated defence strategy is needed. That’s where Microsoft’s Defender for Endpoint comes in.
What is Defender for Endpoint?
Defender for Endpoint is an industry-leading and comprehensive security solution for preventing, detecting and automating the investigation of and response to endpoint threats. Based in the cloud and requiring no additional hardware or software, it supports auto updates which means that all of your business’ endpoints have the latest updates and are protected at all times – without you having to intervene.
Several components define Defender for Endpoint:
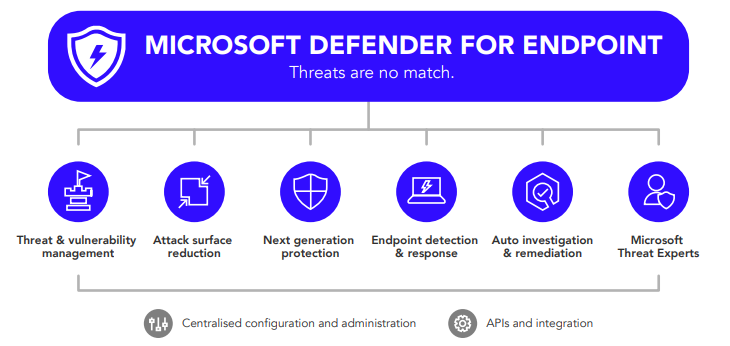
One of the essential capabilities of Defender for Endpoint is EDR.
How does it work?
Defender for Endpoint provides full EDR capabilities that deliver real-time and actionable attack detections. It continually collects behaviours and attacker techniques on the endpoint to identify and alert on suspicious or malicious activity. This includes process information, network activities, user login activities, registry and file system changes, and more.
When a threat is detected, alerts are created in the system for security teams to investigate. Aggregating alerts in this way makes it easy to prioritise alerts effectively, investigate threats, achieve visibility into the entire scope of a breach, and respond directly on the endpoint.
Security teams can also investigate six months of historical data across all endpoints, write flexible queries, save them, and turn them into custom detections. The built-in sandbox also allows teams to submit suspicious files for deep inspection, returning a full report that describes the file’s capabilities.

Conclusion
More people working from home means endpoint security has become far more critical and challenging for businesses. If your business is on the lookout for an effective endpoint protection tool, one backed by Microsoft security experts, Defender for Endpoint is definitely one to consider.
As a leading modern workplace and mobile provider in the UK and a Microsoft Gold Partner for more than 20 years, Daisy successfully defends customers and keeps their businesses safe from the risks posed from endpoint devices. We are one of very few providers to have as many as 14 out of 18 Microsoft Gold competencies, including gold-level Security competency. We can deliver the most appropriate protection to meet your business requirements, including proactive management by our Security Operations Centre (SOC) experts.